Changing the default SSH port and applying a few security best practices can greatly improve the protection of any Linux server against automated attacks. Whether you’re managing a dedicated physical machine or a virtual private server, having full root access gives you complete control over essential security settings.
On our bare metal servers and KVM, you have unrestricted access to configure your SSH service, customize ports, and apply advanced firewall rules to fit your security needs.
How to Change the SSH Port and Enable Security Parameters on Linux Servers
Changing the default SSH port and enabling a few key security settings can significantly reduce the risk of automated attacks on your server. In this tutorial, you’ll learn how to do it step by step.
✅ Requirements
- Root access or a user with sudo privileges
- Console or KVM access (recommended during SSH reconfiguration)
- A text editor installed (such as nano or vim)
1. Log in to the server
Connect to your server using SSH on the default port (22):
ssh root@YOUR_SERVER_IP
2. Edit the SSH configuration file
Open the SSH configuration file:
sudo nano /etc/ssh/sshd_config
3. Change the SSH port
Find the line:
#Port 22
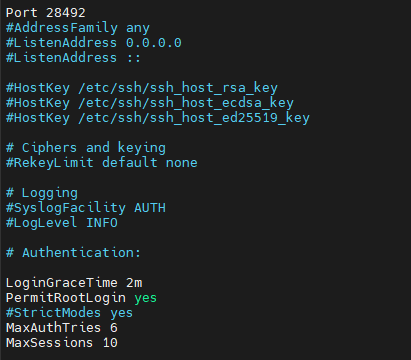
Uncomment it and replace 22 with a new port number — preferably a high, random port. In this example, we’ll use 28492:
Port 28492
⚠️ Avoid common ports like 2222, 8080, or 3306. Choose a number between 1024 and 65535 that’s not used by another service.
4. Enable security parameters with default values
Still in the sshd_config file, look for the following lines and uncomment them (remove the #), keeping their default values:
LoginGraceTime 2m
MaxAuthTries 6
MaxSessions 10
Here’s what they do:
- LoginGraceTime – Limits how long (in seconds) the server waits for login before disconnecting
- MaxAuthTries – Sets how many authentication attempts are allowed before disconnecting
- MaxSessions – Controls how many sessions a single SSH connection can open
Enabling these helps avoid abuse from bots or brute force tools, even if the values are left at their defaults.
5. Allow the new port on the firewall
Using UFW:
sudo ufw allow 28492/tcp
Using firewalld:
sudo firewall-cmd --permanent --add-port=28492/tcp
sudo firewall-cmd --reload
Using iptables:
sudo iptables -A INPUT -p tcp --dport 28492 -j ACCEPT
6. Restart the SSH service
Apply your changes by restarting the SSH daemon:
sudo systemctl restart sshd
7. Test the new SSH port
Before closing your current session, open a new terminal and try logging in with the new port:
ssh -p 28492 root@YOUR_SERVER_IP
If the connection works, you’re good to go.
8. Disable the old port (22)
After confirming the new port is working, you can block port 22 to reduce exposure:
sudo ufw delete allow 22/tcp
# or
sudo firewall-cmd --permanent --remove-port=22/tcp
sudo firewall-cmd --reload
🛡️ Extra Security Tips
To further protect your server, consider the following additional changes in your sshd_config:
PermitRootLogin no
PasswordAuthentication no
AllowUsers your_username
- Disable root login to force use of a regular user with sudo
- Disable password authentication and use SSH keys only
- Restrict SSH access to specific users with AllowUsers





